I last covered fake LinkedIn emails in 2010 – it wasn’t that big a deal.
Apparently going IPO and reaching 150 million users put a target on the company’s back – let’s look at the topic again…
When the email isn’t from who you think it is…
The trick works like this – the criminal sends you an email that looks like it’s from LinkedIn.
If you click on the embedded link to respond, your browser goes to a web site that exploits a loophole in the browsing technology to infect your PC with a virus.
If you click on a link to unsubscribe – same thing.
A picture says it all
And here are two images of fake emails:
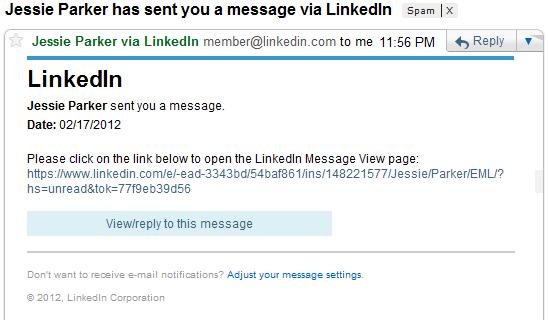
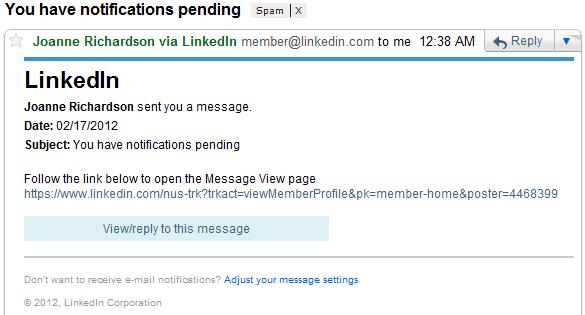
And now for a REAL LinkedIn Email:

Those virus dudes are getting better at it.
In the past, their use of “English as a second language” was abysmal – one could read the email and know that it wasn’t from LinkedIn, or a person from an English speaking country. (BTW – I am trying to insult criminal virus writers from foreign countries – If you want to appear to be John Smith from Anywhere, USA, you really need to know how to write in the English language…)
Detecting fraud
Let’s compare these emails – what discrepancies can you note?
- Bogus subject lines – in both fake emails, the subject line is not something that would come from LinkedIn. It’s created to entice the reader to open the email, but it isn’t “standard”.
- The use of a link to retrieve the message – LinkedIn doesn’t include that sort of a link. When LinkedIn sends you a message, you get the message, not a link to retrieve the message.
- Your email client may very well flag the items as spam – not visible here, but gmail properly detected the spam nature of these messages, sorted them to my spam folder and added a large red banner “warning” (that I edited out). Your email client is probably correct on these sorts of things…
- If you hover over the links, you will see that the location the links actually go to is not what is displayed. This should always be a warning. (I, of course, did not embed any links into this post;-)
And a point about the content of the email – when an actual connection, David, sent me a message, it looked like something he really thought I would want to know. It wasn’t some vague reference or “make money fast” sort of message. I could recognize his name – because I know him.
But these virus / infection messages have a couple things going for them:
- They have the colors and format correct
- They use “View/reply to this message” – just like LinkedIn does
- They include a comment at the bottom to adjust your message settings (which also takes the reader to the virus infection page…)
So it is at least partially understandable how someone may end up clicking on these sorts of links.
Protect yourself
A few things you can do to protect yourself:
- Get an anti-virus / anti-spyware package. It’s just too difficult to operate in today’s networked world without some sort of protection. I don’t really care which one, but have one installed.
- Use good tools. I’m not sure I know which tools aren’t good, but consider a browser other than IE. When I wanted to “safely” check out the web page that the links sent me to, my opera browser said “You really don’t want to go to that page, it will infect your PC. Please reconsider.” (Not those words, but that’s what I heard – and so I decided I really didn’t need to “see” that it was a virus infection page;-)
- When in doubt, go to LinkedIn directly and check your inbox. Every LinkedIn communication – be it a message, InMail, or invitation to connect will be located within your LinkedIn inbox. You can login to LinkedIn and see them all directly. You don’t have to ever click on a link within an email. (this advice probably works for any membership site – go to its communication page)
But most importantly:
Connect to people you know and trust.
Why? Because when you connect to actual people, you have a clue that someone is really using the LinkedIn communication mechanisms to get a hold of you. Your good friend Mary just might be trying to reach you, some random person is not a connection, and so they aren’t likely using LinkedIn to reach you.
Someone wanting to meet you through LinkedIn could reach you with an InMail or an Introduction – and that would look different.
How things have changed – and stayed the same
Long-time readers may remember the post from October of 2010 – here’s a handy link to it just so you can compare the quality of the fake LinkedIn email messages. Better effort from the criminals, but still annoying.
And now you know – and knowing is half the battle;-)
To your continued success,
steve
—
Steven Tylock
http://www.linkedinpersonaltrainer.com
http://www.linkedin.com/in/stevetylock
Thanks for revisiting this! It explains why I started seeing suspicious emails in my personal mailbox from people that I not only didn’t know, but when I looked them up on LinkedIn, they didn’t exist :-) . Being fairly new to LinkedIn, I was unaware of this virus tactic – while I made the mistake of opening one of them, initially, I DO have up-to-date antivirus, spyware, etc. Thanks again, Steve, I’ll be sharing this with my LinkedIn connections.
Glad to be of help Sue.
As a point of interest – I think another batch of spam may be making the rounds. One of my connections and somewhat-frequent suggester of topics has sent me an example of a message he recently received.
Same fake stuff – new expression of an attempted exploit / scam.
steve
Still going around in October 2012… I used to get one or two a day and I don’t use that site so it’s easy to spot the B/S emails. Also – gmail does flag as spam.
Thanks for the comment Kevin.
I’ve been building a batch of “LinkedIn spam that I’ve seen lately” – might be time to post again on the topic…
steve
Came to me this time. What a mess! Now what? How do you remove the virus? You’d think LinkedIn would care – I’m closing my account and hope that others will do the same. Very sad for everyone and for LinkedIn. There needs to be a way for businesses to fight back and really care about these issues. Stay away from social media I guess.
PM,
You understand the email is fake, right?
It wasn’t from LinkedIn, and had nothing to do with the site except that the scammers made it look like it came from LinkedIn.
I don’t have any specific advice for you about the virus – you could try AVG free, and the Microsoft Safety Scanner is a good one time sweep.
steve
I received a fake invitation email (I don’t have a LinkedIn account), Subject: Invitation to connect on LinkedIn. I’m worried because the company who the email stated was supposedly inviting me is a company that I have been in contact with, the exact company name and full owners name were used. All the example phishing LinkedIn emails I have seen posted online have had a generic name like John or Bob as the inviting LinkedIn user. Should I be be at all concerned with the trustworthiness of the actual company? Any thoughts or information will be greatly appreciated.
Matt
Matt,
You say it’s a fake, but it’s from an actual person you know.
I think it’s probably a real invitation – but since you don’t use LinkedIn, if you were to click on that link, you would go to LinkedIn and be asked to create an account. (which might look like spam since you don’t seem to want an account;-)
The fake emails I’m talking about above don’t go to LinkedIn – they’re made to look like actual LinkedIn invitations, but if you click on them, you go to a web site that tries to give you a virus (or something).
On the actual invite – I tell people (that want to use LinkedIn) to only connect to those they know and trust. It doesn’t sound to me like you know and trust this individual yet, but perhaps they trust you.
So feel good that this person trusted you enough to try to connect, but since you don’t use LinkedIn, there isn’t anything that you can do with the invitation.
steve
(It’s kind of like when people ask me to connect to their facebook account or page – I just let it go…)